UNDERSTANDING THE PREVALENCE OF PASSWORD REUSE
Recent LastPass analysis reveals a startling trend: 60% of network users likely reuse their passwords across multiple applications. This practice persists despite growing cybersecurity threats and increasing data breaches. Companies invest heavily in network security education, yet the password reuse issue remains widespread.
WHY DO EMPLOYEES REUSE PASSWORDS?
- Pressure for Productivity: In a high-paced work environment, using the same password seems faster and simpler.
- Memory Ease: Frequently used passwords are easier to remember.
- Underestimation of Risks: Many workers don’t view password hygiene as a crucial aspect of their job.
- Cognitive Challenges: Studies indicate that people struggle with multitasking, influencing their password management choices.
DOING NOTHING CAN MEAN LOSING EVERYTHING
Reusing passwords can trigger a cascade of security breaches, putting entire organizations at risk. Accounts, applications, and systems become vulnerable, potentially leading to significant losses.
CHANGING HABITS: A PSYCHOLOGICAL CHALLENGE
Altering employee password habits is a complex task that involves understanding human psychology. Traditional methods of change may not suffice in the digital realm.
THE HACKER THREAT: A CONSTANT SHADOW
Hackers are ever-present, waiting to exploit weak cybersecurity practices to access sensitive customer data and financial records.
INTRODUCING LASTPASS FOR ENHANCED PASSWORD MANAGEMENT
LastPass offers a robust solution to password management challenges:
- Automated Generation of Strong Passwords: Create and manage unique, complex passwords for each account.
- Convenient and Secure Access: Use LastPass autofill for safe, quick logins across various platforms.
- Centralized Control: Administer and enforce password policies effectively.
- Cross-Device Synchronization: Access passwords anywhere using LastPass extensions and apps.
- Master Password Guidelines: Follow strict protocols for creating and storing master passwords.
ENFORCE BEST PRACTICE WITH LASTPASS
With best-practice password management via LastPass, password policy offenders can contribute to compliance, still switching attention back to priority tasks at pace, by eliminating the need to remember myriad passwords and codes.
- Generate, store and manage unique and complex passwords for each individual account – without users needing to store them elsewhere or remember them.
- Log in fast, anywhere, to multiple applications and accounts safely by leveraging LastPass autofill, removing the need to manually enter passwords online.
- Centrally control and administer employee passwords, enforcing protocols, policy and best practice – and securely share credentials if needed.
- LastPass subscribers can access their passwords anywhere on any device synchronised via the LastPass browser extension and app. Of course, stringent guidelines should be followed when it comes to master password creation, storage and practice.
SECURE PASSWORD MANAGEMENT – ENHANCED
Account security at LastPass has taken another leap forward for 2024 with enhanced master password practices: all users must now re-enrol multi-factor authentication (MFA) and update master password length and complexity – increasing defence against ever-evolving cyber threats. Advances in password cracking and brute-force technology and techniques mean that the National Institute of Standards and Technology (NIST) standard eight character minimum for passwords is no longer enough.
With LastPass, no fewer than 12 characters are now permitted for master passwords.
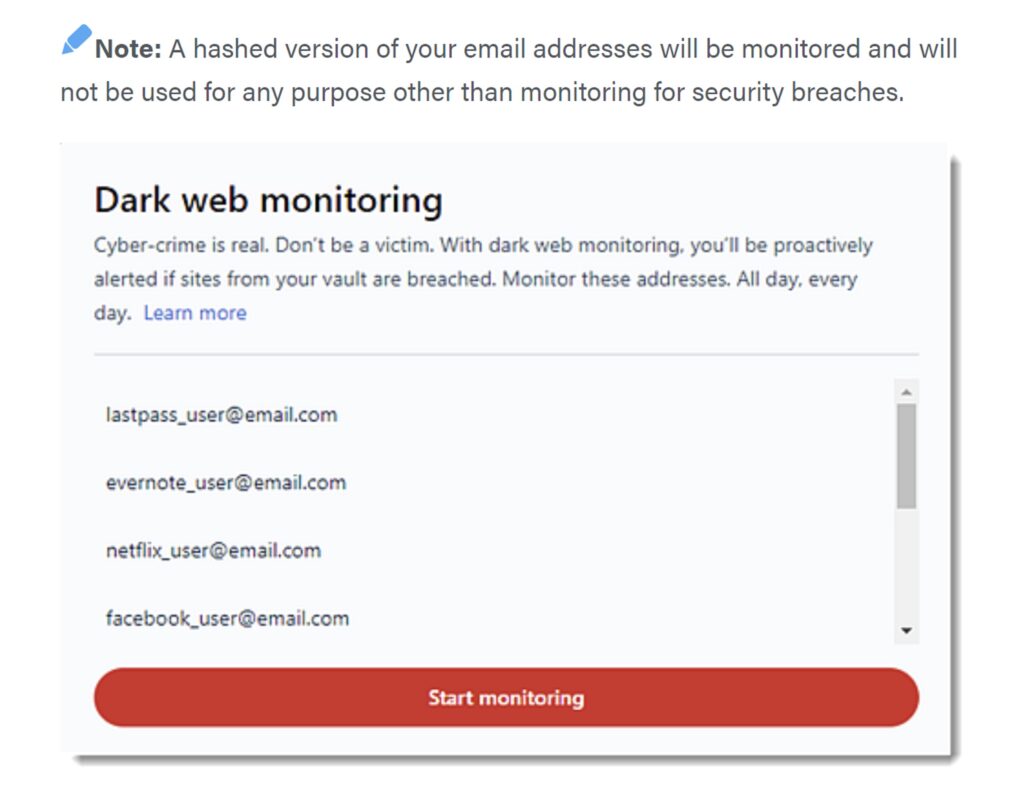
Coupling this newly enforced requirement are PBKDF2 iteration increases, empowering customers with stronger and more resilient encryption keys for accessing and encrypting their LastPass vault data. In addition, LastPass will now check new or reset master passwords against a database of known breached credentials, fending off previous dark-web exposure. If found, the customer will be prompted to choose another password. Click here for how to enable dark web monitoring.
Modern password crackers can ingest lists of known passwords as part of their dataset, slashing cracking time. Sensitive data stored within a user’s LastPass vault is encrypted using a unique master password-derived encryption key that LastPass itself does not possess.
BEST PRACTICE FROM JANUARY 2024
- Master passwords of 12 characters, including at least one upper case, one lower case, one numeric, and one special character value.
- Combinations can be memorable, but should still be difficult to guess.
- Each password should be unique to each individual user.
- Do not use email addresses or incorporate other personal information.
- Do not use sequential characters such as QWERTY or 1234 – or repetition such as AAAA or 77777.
- Do not reuse master passwords for any other account or application.
- Set up account recovery before changing master passwords, with multiple options provided including biometrics, mobile, SMS and recovery one-time passwords. Here’s how – alternatively, view this five-minute video.
Click here to download a PDF containing fuller technical and compliance details from LastPass.
NOT YET A CUSTOMER?
Contact QBS for more information.
- Email us: [email protected]
- Call us:+44 (0) 20 8733 7100
